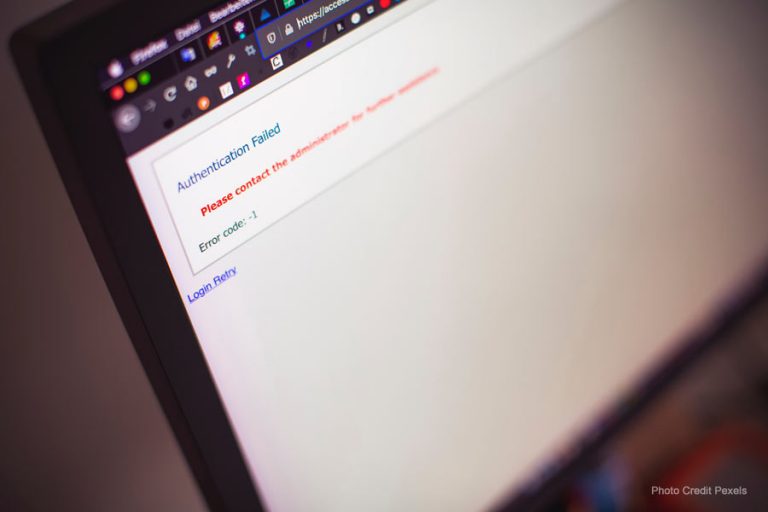
Simple Ways to Boost Your Data Security
Data security and privacy are tremendous concerns in the business world. Nearly three-quarters of CEOs in the United States reported in 2021 that they are “extremely concerned” about cyber threats. This concern ranked higher than health crises and the pandemic – and for a good reason. The digital landscape is going through massive transformation on…