
We are happy to conduct an onsite walk through and assessment of your IT system, the robustness of your data recovery and restoration capabilities, and the realistic benefits to deploying a digital–transformation strategy for your IT system.
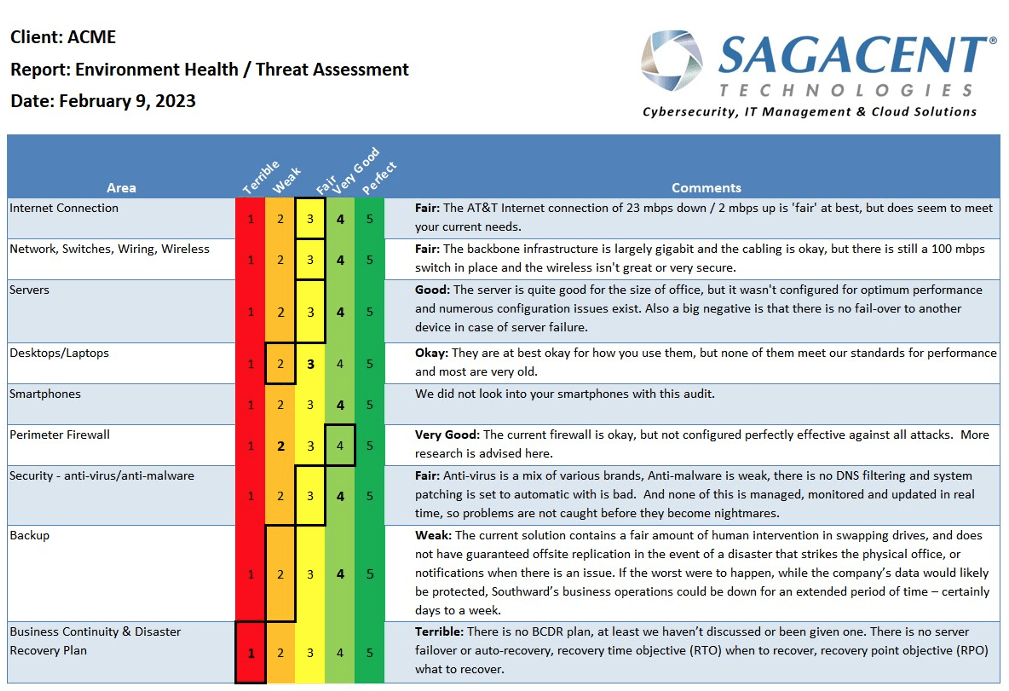
Using industry-specific guidelines, our experienced group of IT professionals will survey your IT environment, collect details on system volume, user support demand, and cyber resistance. We will also assess your data back-up and restoration capabilities, and compare it to others in your industry.
Our simple proprietary report will allow you to see where additional investment will be most productive and what upgrades would be especially critical for your company.
Request Your Free Assessment
Sign up for this valuable assessment at no charge.
